This report provides a holistic view of cloud security’s evolution, tracing its major milestones, a detailed breakdown of the key vendors today, and evolving market shifts. It presents a new framework for redefining Cloud Native Application Protection Platforms (CNAPP), addressing its limitations and contradictions while offering a comprehensive roadmap to navigate the future of cloud security.
Key Actionable Summary
Here are the key takeaways:
-
Evolution of Cloud Security Vendors: This report explores the evolution of cloud security vendors over the past 14 years, taking you through how we got to this critical juncture and using historical context to build a vision for the future.
-
Consolidation Trends: We discuss the consolidation trends as cloud security vendors merge adjacent solutions, particularly in Application Security and SOC operations, and analyze why some vendors have outperformed others.
-
In-depth Vendor Analysis: We provide in-depth analysis of companies like Wiz, CrowdStrike, SentinelOne, Orca, Upwind, Sweet Security, Palo Alto Prisma Cloud, Jit, Rad, and Armo as representative players in the evolving nature of the CNAPP market.
-
Limitations of CNAPP: Beyond merely categorizing vendors, we discuss limitations of the current conception of CNAPP as an all-in-one security platform. We propose some new perspectives to try and address the following contradictions in the market:
- Increased Spending, Decreased Satisfaction: Despite rising cloud security budgets, end-users remain dissatisfied.
- Feature Overload: The most successful CNAPP platforms offer fewer features, even though demand for functionalities has grown.
- Agentless vs. Agents: Companies that once championed agentless solutions are now all building agents.
- Developer vs. Security Analyst Personas: CNAPP tools are used by developers and analysts, despite these personas having vastly different needs.
- Old Innovations in New Packaging: Code scanning and runtime security are being hailed as breakthroughs, but they’ve been around for years. The market wasn’t ready for them yet, is it ready now?
-
Market Growth: The Cloud Security market continues to grow and proves to be an unavoidable reality for legacy providers, who push forward acquiring their way into the market.
-
CNAPP Feature Expansion: The CNAPP feature set continues to expand, with analysts both lamenting the complexity while pushing for the category to be an all-in-one solution. CNAPP also struggles to span across posture and runtime, as enterprise security companies struggle to address all aspects of security in a single platform.
-
Demand and Frustration: There is still demand for cloud security tools, with companies viewing these solutions as the cornerstone and beginning of their security program. However, practitioners and CISOs alike are frustrated with the tools they have. There are too many tools, and too few results.
-
Practitioner Frustration: Practitioners are frustrated by a lack of context, alert fatigue, and the general pain of having small teams manage the security tests and detections for teams 100x their size. They’re being expected to understand the details of an impossible number of infrastructure configurations.
-
CISO Frustration: CISOs are frustrated with the wasted time and developer complaints, all without much to show for it. Their teams have to spend hours troubleshooting alerts, and many cloud breaches go totally undetected by their CNAPP.
-
Future Trends: This is our first report on the market’s state. In our next report, we’ll explore future trends, themes, and predictions of how we think the market will evolve.
Our report offers an honest assessment of where the market stands today and where it’s headed, helping you navigate the complex and ever-evolving world of cloud security.
Brief History of Cloud Security
The core of pre-cloud security was only two solutions: endpoint detection response (previously antivirus) and network security via firewalls. These core technologies birthed the largest mass-market companies as their leaders, CrowdStrike and Palo Alto Networks.
In the early days of the cloud, vendors rushed to deploy their existing solutions into this new environment. Only early visionaries saw that the transition to the cloud actually opened a section of the data center to security that was previously unavailable: the end-to-end configuration of the resources themselves.
As security teams evolved, the question became less “how can I take my existing tool and run it in the cloud” and more “how can I figure out what the heck is going on up there?” Discovery and context became more urgent needs than porting existing tools that never quite worked right. Basic EDR functionality and basic network protection now also came out of the box with GuardDuty, Security groups, and other native capabilities in AWS.
Security teams were frankly late to the party, realizing only later that the workloads themselves in the cloud were shifting from servers to containers. Existing players had massively invested in Windows protection, with very little support for Linux at the time, never mind the container layer. Beyond just needing Linux support, teams needed deeper visibility into containers.
Evolution of Cloud Security
Innovators saw the opportunity across two areas: access to the cloud APIs for visibility and the need for container insights. Cloud Security has changed massively in the past 10-14 years, trying to evolve and maximize the power of these two seemingly simple innovations. Early vendor “CSPM” products quickly became commoditized, as interrogating cloud APIs for misconfigurations became common fodder for open-source projects like Prowler or ScoutSuite.
Even in these early days, the split between posture and runtime was apparent but never fully understood by the industry. Rather than positing some hidden genius behind the approaches of these early companies, it’s more likely that a combination of luck, agility, and connections helped cement the early discussion of cloud security into agent vs. agentless instead of posture vs. runtime.
Pivotal Moments in Cloud Security
- The 2010-2014 (CSPM and the Shift to Cloud): Early focus on compliance checks and governance solutions for cloud environments.
- 2015 – 2018 (Innovations in Workload Security): Emergence of container security and securing cloud-native applications.
- Post 2018 (Synergies around CNAPP): Cloud security consolidation and the introduction of agentless side scanning.
Summary of the evolution
Cloud security has evolved in three clear phases:
- The era of cloud posture and misconfigurations (2010-2015).
- The era of runtime experimentation (way ahead of its time) as containers, and microservices grew in adoption (2013-2018).
- The era of agentless scanning and consolidation (2019-2023)
The next great question of Cloud Security is asking what teams want more – further consolidation or better results with fewer features.
Deployment options for cloud security (Agent vs Agentless)
One of the central discussion points about the evolution of cloud security is how much the role of agents and agentless played throughout the history, and how relevant the question is today. There is no doubt, the pivotal moment was the introduction of agentless scanning by companies like Orca and Wiz. Agentless scanning was a turning point – but anyone who tells you they knew it at the time is lying.
When organizations move to the cloud, their first problem is visibility – AWS just shows them a bunch of EC2 instances without even names to identify what they’re doing. They have two deployment options to scan for vulnerabilities, and just get general insights into these workloads:
- Agent
- Agentless
Evaluating Agent-based solutions in 2024 (The Return of Agents?)
Here’s what matters for professionals thinking about agents in 2024: performance has gotten better, insights have improved, and installation has gotten easier.
Pros
- Real-Time Threat Detection: Agents can detect and mitigate threats in real-time, allowing security teams to respond to incidents faster.
- Granular Data: Agents are useful for everything from reachability analysis to looking for non-human identities in application contexts.
- Deep Visibility and Control: Agent-based solutions offer granular visibility into the behavior of the underlying workloads, processes, and system files.
- Containers. Period: Containers are the infrastructure of the cloud, powering the vast majority of cloud workloads.
- Emergent Application Layer Detections: The most innovative agent-based solutions are reaching deeper into the application running on workloads themselves, giving robust visibility security teams have never before had access to.
Risks
- Deployment: Traditional agents struggle with complex deployment and maintenance.
- Performance Questions: Container monitoring solutions rely on new implementations and experimentations with eBPF and other telemetry solutions.
- Workload Edge Cases: At this point, most vendors support Kubernetes, and self-hosted container deployment solutions. However, there are workload edge cases such as serverless and PaaS where agents struggle to accomplish much.
- Response Anxiety: Many companies tense up when it comes to the idea of allowing automated response actions, due to bad histories with other vendors or solutions.
How Agentless Scanning Emerged
Orca launched the first version of agentless side scanning, which allowed deep visibility into cloud workloads without the need to install agents. Subsequently, Wiz was able to make the experience more intuitive with the graph and more fully bring the approach to market.
Pros
- Quick Deployment and Rapid Time-to-Value: Agentless solutions are easier to deploy since they do not require installing software on each workload.
- Good Context Without an Agent: Beyond the snapshot scanning, agentless solutions are able to build full cloud attack graphs, look at network traffic with flow logs, perform secrets scanning, and really function as full asset management systems.
- Suited Toward Multi-Cloud and Multi-OS: Agentless solutions are particularly suited for organizations that operate across multiple cloud platforms with multiple workload types.
Limitations
- Work Generators: Agentless solutions discover all sorts of problems – some of which are real, some of which aren’t. But ultimately, they don’t independently solve a single problem.
- Containers are Ephemeral: Agentless scanning doesn’t fit the containerized world well, because many containers run for only seconds at a time.
- Efficacy and High False Positives: Agentless solutions rely on data collected from cloud APIs which don’t have workload data, and sometimes are missing relevant security data altogether.
- Hidden Lack of Support: Agentless scanning of underlying system volumes is amazing!…when systems have underlying volumes.
- Hidden Costs: Snapshot storage and network transfers (depending on configuration) ain’t free!
Overall, the story of CNAPP is the story of security teams looking for agentless visibility solutions, before maturing into agent-based ones as they learn that their cloud is mostly containers.
Frameworks For Understanding Cloud Security Today
CNAPP by Gartner
Enterprises, along with analyst firms, continue to push the idea that CNAPP means all in one security. One fascinating dichotomy are these articles from Forrester which we’d argue contradict.
Cloud Security Posture Management (CSPM)
Gartner explains that CSPM as tools are designed to identify misconfiguration issues, gaps in security policy enforcement, and compliance risks in the cloud by comparing cloud environments against a predefined set of best practices stated policies, and known security risks.
Cloud Workload Protection Platforms (CWPP)
CWPP was always a weird category, because it was just EDR but it worked on containers. In a phrase, CNAPP = Redlock (CSPM) + Twistlock (CWPP). CSPM provides the cloud visibility, CWPP provides the container visibility. This term has grown less commonly used because of the lack of clarity. We prefer Cloud Detection Response (CDR), meaning providing detection and response across cloud and workload layers.
Limitations of CNAPP
CNAPP at this point has become bloated to the point of mockery. I’ve seen demos where vendors click 6 screens deep to show a giant table of application layer vulnerabilities. Finally, what practitioners have always wanted, even more vulnerabilities that don’t matter.
Developers and Security Operations don’t want the same things
Developers want (or are forced) to see vulnerabilities in their code, and how those vulnerabilities were picked up in production. Conversely, security operations teams live in the SIEM. They query logs to respond to attacks and put stories together.
Defining a Security Engineer?
No two security engineers are really alike. CNAPPs have really only served cloud security engineers by providing asset visibility but will really struggle to appease more holistic practitioners who have evolved deeper into application security.
The Future of CNAPP?
CNAPP has created a crappy version of too many standalone products and is at a serious breaking point. Providers have forced themselves into having to dive head first into runtime protection and ASPM at the same time. They risk getting caught in the middle and made obsolete by both.
How We Should Think of CNAPP
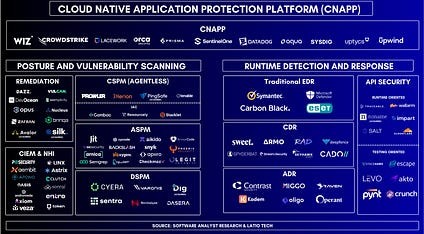
This is our proposition for the CNAPP mental model: a series of functionalities aligning either to vulnerability detections or aligning to runtime exploit detections. At the highest level though, there are only two fundamental capabilities – either you’re detecting vulnerabilities, or you’re responding to threats.
- Posture and vulnerability scanning: This area primarily focuses on proactively identifying misconfigurations and vulnerabilities in cloud environments before they can be exploited.
- Runtime detection and response: This primarily monitors cloud workloads and applications in real-time, detecting active threats and anomalies as they happen.
Vendor Landscape & Ecosystem Discussions
Based off the CNAPP acronym we have laid out above, we believe there are different vendors to depict different components of the market. The vendor list we have included at the bottom is not an exhaustive list of all the vendors.
Major Vendors
Wiz
Wiz launched in 2020 as the last major entrant to the CNAPP market, addressing the most basic yet essential cloud security need—cloud visibility via agentless vulnerability scanning. This simple requirement came with complex implementation challenges, but Wiz executed on it exceptionally well, outperforming its competitors at the time.
Product Advantages
- Graph User Experience: Wiz’s graph model allows security teams to understand these complex relationships in a highly efficient way, querying the relevant information for the relevant teams.
- Evolving Beyond Agentless Scanning: Wiz launched a much more effective agentless scanner that helped teams identify vulnerabilities with incredible quick time-to-value and deployment for the largest enterprises.
- Attack Path Analysis: Wiz’s graph-based system naturally supports attack path analysis.
- Effective Prioritization Engine: Wiz’s prioritization engine was an early attempt to correct this problem.
- Customization and Ease of Collaboration: Customers frequently highlight Wiz’s user-friendly interface and automation features, which allow security teams to quickly prioritize critical issues, and create common dashboards with engineering teams.
- Branding: Wiz has built a strong GTM organization around partners, CSPs, and unlocking large enterprise accounts. This is similar to what we saw in Endpoint security with Crowdstrike vs. SentinelOne.
Areas To Watch
- Depth of Agent-based Capabilities: While Wiz excels in agentless scanning, it has not fully matched the deep workload visibility and runtime protection offered by their competitors based off our customer discussions.
- ASPM and Code Scanning: Other vendors have introduced their own SCA and SAST scanning, but this seems to have done little to move the market, as the offerings are really limited compared to full application security products.
- Serving Multiple Personas: Most CNAPP platforms have been built for cloud security engineers, who typically have systems engineering or DevOps backgrounds.
- Pricing: Though competitively priced, Wiz is not the cheapest solution. Early adopters benefited from discounts, but newer customers have found pricing less flexible.
Crowdstrike
Crowdstrike launched their cloud security solution in October 2020.
Product Advantages
- Windows-based environments: Many security teams falsely assume that an agent is an agent, and that their existing CrowdStrike licenses can easily be expanded into the cloud.
- Discounting: CrowdStrike was noted for offering flexible licensing options that allowed organizations to scale up or down based on changing needs.
Areas To Watch
- Doesn’t Meet Cloud Engineer Goals: CrowdStrike’s entire user experience is built around a very specific user: operations teams responding to runtime threats via process trees, quarantining, and similar heuristics.
- Overhead around agents: Despite its strengths, CrowdStrike’s reliance on agent-based security solutions can increase operational complexity, overhead, and costs, especially for DevOps teams that need to manage manual configuration for each cloud subscription or workload.
- Limited cloud coverage: CrowdStrike’s CSPM also suffers from limited cloud coverage, supporting only AWS and Azure.
- Onboarding process: CrowdStrike’s onboarding process has been noted as complex and time-consuming, requiring significant manual configuration, which can slow down deployment in dynamic cloud environments.
Palo Alto Networks Prisma Cloud
Palo Alto had the first vision of CNAPP.
Comprehensive solution set
Prisma Cloud stands out as one of the most robust platforms (currently over 13+ modules across cloud and application security), offering security coverage across multi-cloud environments, containers, workloads, and code security with both agent and agentless solutions.
Areas To Watch
- Lacking An Integrated and outcome-driven vision: From what we’ve heard from practitioners, Palo still lacks a fully integrated risk view, and they have higher false positive rates than competitors like Wiz and Orca.
- Customization Comes at a Cost: While the flexibility through RQL (RedLock Query Language) allows for custom security policies, Prisma Cloud’s heavy reliance on manual rule-based configurations makes it more resource-intensive.
- Higher False positives: We heard multiple times that Palo Alto also has a higher false positive rate than solutions like Wiz or Orca.
Orca
Orca Security made a big leap in cloud security with the introduction of its patented agentless SideScanning technique in 2019.
When it comes to its feature set and user experience, the comparison to Wiz is inevitable. Orca continues to go toe to toe with Wiz on its agentless feature set. There are real benefits to Orca: their data architecture is more scalable, they’ve continued to push agentless capabilities and offer very comparable risk graphs.
SentinelOne
By acquiring PingSafe, SentinelOne is stepping into CNAPP with a big bet.
Sysdig
Sysdig has long been a go-to tool for DevOps engineers and enthusiasts.
Upwind
Upwind was founded in 2022, one of the latest cloud security vendors.
Sweet Security
Sweet Security focuses on cloud-native runtime security. Their key offering utilizes an eBPF sensor designed to help organizations detect and respond to active cloud threats in real-time.
Example of Code to ASPM: Jit
Jit is an ASPM (Application Security Posture Management) platform designed to empower developers to own the security of their code.
CSPM as Part of ASPM
An emerging trend among companies that began with shift-left security is the integration of CSPM (Cloud Security Posture Management) into their offerings. Jit is no exception.
Connecting Code to Cloud
By integrating Jit’s automated code scanning and vulnerability detection into CI/CD pipelines, cloud security teams can ensure security is applied consistently across all development teams.
Cloud Detection & Response (CDR)
Cloud Detection and Response tools detect malicious activities in common cloud workloads (containers & Kubernetes) and contextualizes them with other cloud services to create a single attack path across cloud environments.
Armo
ARMO provides protection from cloud runtime threats with both posture and runtime detection solutions.
Rad Security
Rad security is an amazing growth story in CNAPP.
Application Detection & Response (ADR)
Application Detection and Response (ADR) offers security teams visibility, detection, and response across their applications.
Miggo
Miggo is one of the only offerings in the ADR space to look at applications holistically by leveraging distributed tracing.
Oligo Security
Oligo Security took an elegant approach to extend detection capabilities into applications, without requiring any app-level instrumentation.
Raven.io
Raven has taken the approach of looking for application attacks by monitoring application and library activity.
Kodem
Kodem has built their own distinct solution in the ADR space that focuses on the local application context but is more emphasizing how their runtime detection mechanisms can be used to reduce vulnerability false positives.
Operant
Like many vendors in this space, Operant could also easily fit within the API or CDR categories.
Remediation
Dazz Security
While many companies have invested heavily in Cloud Native Application Protection Platforms (CNAPP), they often struggle to manage the flood of alerts and issues generated by cloud logs or the security tools themselves.
Dazz’s Core Differentiators
- Data Correlation and Root Cause Analysis – Dazz excels at normalizing and correlating data from different development, infrastructure, and security tooling.
- Remediation Guidance and fixes – Dazz gives developers insights into security issues, recommended fixes, and actions to fast track remediation.
Unified Remediation & ASPM
Dazz integrates seamlessly with leading CNAPP platforms and contextualizes them further with additional context from development, application security testing (AST), and other tools.
Root Cause Analysis: Fixing What Matters
Dazz’s advanced root cause analysis capabilities help organizations address vulnerabilities efficiently.
Concluding Thoughts
We believe the conversation around CNAPP will continue to evolve over the next few years, and the goal of this report was to help frame those future developments.
Moving forward, we believe there are some critical questions for the industry.
- Are security teams truly ready to move beyond “just visibility?”
- Can you make a UX for developers and the SOC in the same platform?
- Lastly, the discussion around platform consolidation continues to evolve.
Ultimately, the vendors that solve these questions for customers will continue to win the market.