Is There Guided Access For Samsung devices? Yes, while Samsung phones and tablets don’t have a feature called “Guided Access” like Apple’s iOS, there are alternative solutions that can provide similar functionality. CONDUCT.EDU.VN offers expert guidance and resources to help you navigate the best options for restricting device usage on Samsung devices, ensuring focus and security. Discover the power of kiosk mode and app pinning with trusted compliance standards.
1. Introduction: Guided Access and its Android Equivalent
Guided Access is a feature initially developed by Apple for iOS devices, providing a way to lock a device into a single app. This is extremely useful in a variety of scenarios, from educational settings to business environments where focus and security are paramount. While Samsung, running on the Android operating system, doesn’t have a direct “Guided Access” feature, the need for similar functionality exists. The primary method for achieving single-app mode on Android is through Screen Pinning, a native Android feature. However, for more robust control and enterprise-level management, organizations often turn to Mobile Device Management (MDM) solutions. These solutions, as explored further at CONDUCT.EDU.VN, provide advanced capabilities to restrict device usage, manage security policies, and enhance user productivity.
2. Understanding Screen Pinning on Android and Samsung
Screen Pinning is the built-in Android feature that serves as the closest alternative to Apple’s Guided Access. It allows you to lock a device to a single application, preventing users from navigating to other apps or accessing system settings without a designated PIN or gesture. This can be highly beneficial in scenarios where you want to limit distractions or ensure that a device is used for a specific purpose.
For example, a teacher can pin an educational app on a tablet given to a student, preventing them from accessing games or other distracting content. Similarly, a business can pin a point-of-sale (POS) app on a device used by employees, ensuring that it is solely used for transactions.
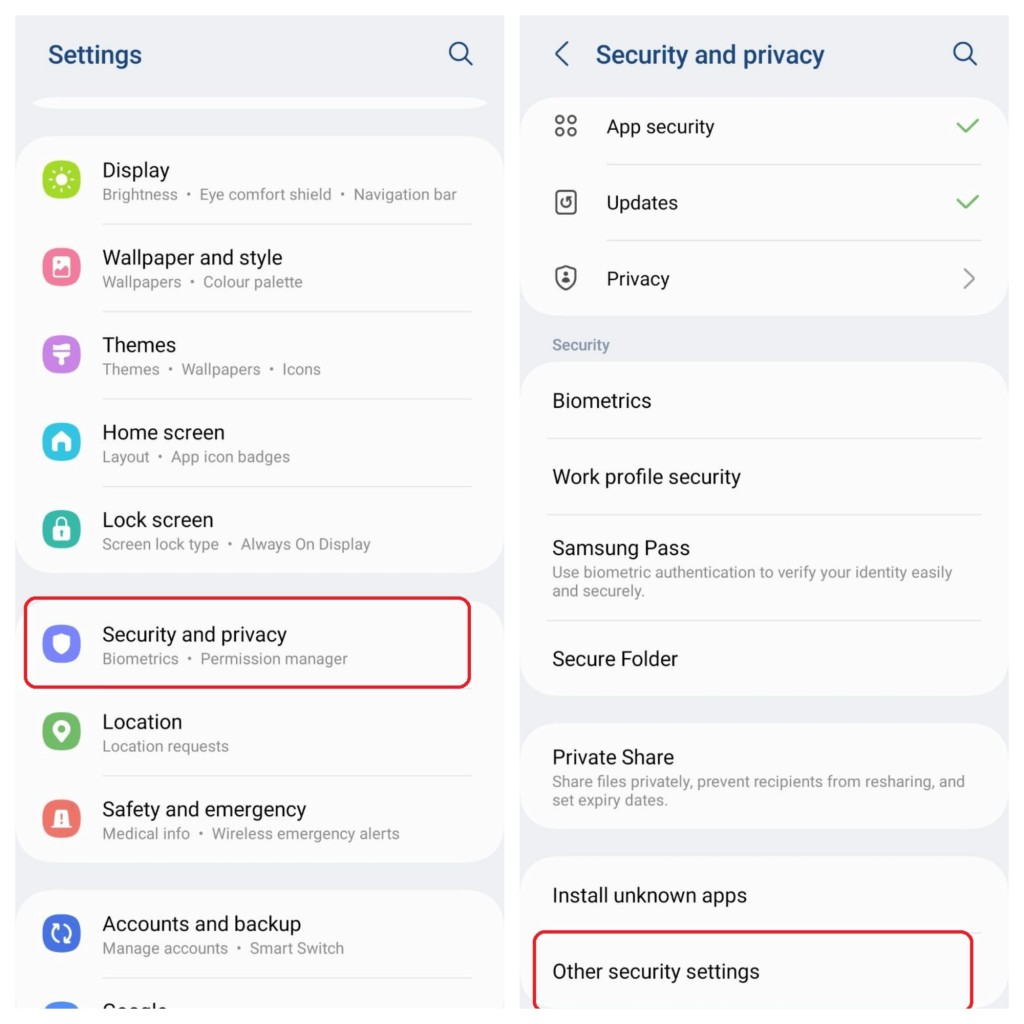
2.1. How to Enable Screen Pinning on Samsung Devices: A Step-by-Step Guide
The process of enabling and using Screen Pinning on Samsung devices is relatively straightforward:
- Open Settings: Navigate to the Settings app on your Samsung device.
- Go to Security (or Security and Privacy): The exact wording may vary depending on your Android version.
- Find Pin Windows (or App Pinning): Look for an option related to pinning or locking apps. It may be under “Advanced settings” or “Other security settings.”
- Enable Pin Windows: Toggle the switch to turn on the Screen Pinning feature.
- Pin an App:
- Open the app you want to pin.
- Open the Recent Apps screen (usually by swiping up from the bottom or tapping the recent apps button).
- Tap the app icon at the top of the app preview.
- Select “Pin this app.”
After completing these steps, the selected app will be locked to the screen. To unpin it, you’ll typically need to press and hold the Back and Recent Apps buttons simultaneously.
2.2. Limitations of Screen Pinning
While Screen Pinning is a useful feature, it does have limitations:
- Basic Functionality: It primarily locks the device to a single app and offers limited control over hardware buttons or specific screen areas.
- Security Concerns: Depending on the device’s settings, it might be possible to exit Screen Pinning without a PIN or password, especially if the user knows the correct button combination.
- Management at Scale: Configuring Screen Pinning on multiple devices can be time-consuming and impractical for large organizations.
- Lack of Advanced Features: Screen Pinning lacks advanced features such as remote management, device tracking, and the ability to customize the user experience.
3. MDM Solutions: A Robust Alternative for Samsung Guided Access
For organizations that require more comprehensive control over their Samsung devices, Mobile Device Management (MDM) solutions offer a powerful alternative to Screen Pinning. MDM software allows IT administrators to remotely manage, secure, and monitor devices, providing a wide range of features that go beyond the capabilities of Screen Pinning.
3.1. Key Benefits of Using MDM for Samsung Device Management
- Remote Management: MDM solutions enable IT administrators to remotely configure settings, install apps, and update software on devices, regardless of their location.
- Security Policies: MDM allows you to enforce security policies such as password requirements, data encryption, and remote wiping to protect sensitive information.
- Kiosk Mode: MDM can lock devices into kiosk mode, which restricts access to a single app or a pre-defined set of apps. This is ideal for dedicated-purpose devices used in retail, hospitality, or transportation.
- Device Tracking: MDM solutions can track the location of devices, helping to prevent loss or theft.
- Application Management: MDM provides control over which apps can be installed and used on devices, ensuring compliance with company policies.
- Content Management: MDM enables you to distribute documents, videos, and other content to devices, ensuring that users have access to the latest information.
3.2. How MDM Solutions Enhance Security and Productivity
MDM solutions enhance security and productivity in several ways:
- Data Protection: By enforcing security policies and providing remote wiping capabilities, MDM helps to protect sensitive data from unauthorized access.
- Compliance: MDM ensures that devices comply with industry regulations and company policies, reducing the risk of fines and legal issues.
- Focused Work: Kiosk mode and application management features ensure that employees use devices for their intended purpose, increasing productivity and reducing distractions.
- Streamlined Operations: Remote management and automation capabilities streamline IT operations, reducing the time and resources needed to manage devices.
- Improved User Experience: MDM can customize the user experience by providing access to the right apps and content, improving user satisfaction and engagement.
3.3. Examples of MDM Solutions for Samsung Devices
Several MDM solutions are compatible with Samsung devices, including:
- Scalefusion: Known for its user-friendly interface and robust kiosk mode capabilities.
- MobileIron: A comprehensive MDM solution with advanced security and compliance features.
- VMware Workspace ONE: A unified endpoint management platform that supports a wide range of devices and operating systems.
- Microsoft Intune: A cloud-based MDM solution integrated with Microsoft 365.
4. Implementing Kiosk Mode on Samsung Devices via MDM: A Detailed Guide
Kiosk mode is a particularly valuable feature offered by MDM solutions. It essentially transforms a Samsung device into a dedicated-purpose kiosk, limiting access to a single app or a curated selection of apps. This is perfect for scenarios like digital signage, point-of-sale systems, interactive kiosks, and more.
Here’s a general overview of how to implement kiosk mode using an MDM solution:
Step 1: Choose an MDM Solution and Enroll Your Devices:
- Select an MDM solution that meets your needs and budget.
- Follow the MDM provider’s instructions to enroll your Samsung devices into the MDM platform. This usually involves installing an MDM agent app on each device.
Step 2: Create a Kiosk Profile:
- Within the MDM platform, create a new profile specifically for kiosk mode.
- Give the profile a descriptive name (e.g., “Retail Kiosk,” “Digital Signage Player”).
Step 3: Configure Kiosk Mode Settings:
- Single App Mode or Multi-App Mode: Choose whether you want to lock the device to a single app or allow access to a specific set of apps.
- Allowed Apps: If using multi-app mode, select the apps that users will be able to access.
- Hardware Button Control: Configure whether to disable hardware buttons like the Home, Back, and Volume buttons. Disabling these buttons prevents users from exiting kiosk mode.
- Screen Orientation: Set the desired screen orientation (portrait or landscape).
- Idle Timeout: Configure an idle timeout, which will automatically return the device to the kiosk app after a period of inactivity.
- Password Protection: Set a password or PIN to prevent unauthorized users from exiting kiosk mode.
Step 4: Deploy the Kiosk Profile to Your Devices:
- Select the devices that you want to apply the kiosk profile to.
- Deploy the profile to the selected devices through the MDM platform.
Step 5: Test the Kiosk Mode Configuration:
- Once the profile is deployed, verify that the devices are successfully locked into kiosk mode.
- Test all the allowed apps and features to ensure that they are working as expected.
The specific steps and options may vary depending on the MDM solution you are using, but this general guide provides a solid foundation for implementing kiosk mode on your Samsung devices.
Example using Scalefusion:
Step 1: After you log into your Scalefusion account, navigate to the Device Profiles & Policies. Click on Device Profiles.
Step 2: Click on Create New Profile and create an Android Kiosk/Agent Profile.
Step 3: Set the device in Launcher Mode and select the app that you want to run in Single App Mode.
Step 4: Navigate to Kiosk/Launcher Settings > Single App Mode; Choose the application from the dropdown list.
Step 5: Click on the checkbox – Run All the Time. This option allows the selected app to run on the device without relaunching the app.
Step 6: Now, click on Create Profile to create the profile and apply it on the devices. You have successfully set your device in Single App Mode
Associate the kiosk mode profile with the required Android devices to implement the equivalent of Guided Access for Android.
5. Use Cases for Samsung Guided Access Alternatives
The ability to restrict device usage on Samsung devices has a wide range of applications across various industries and scenarios:
5.1. Education
- Classroom Tablets: Lock tablets to educational apps and websites, preventing students from accessing distracting content during lessons.
- Testing and Assessments: Ensure that students can only access the testing app during exams, preventing cheating and maintaining test integrity.
- Special Education: Simplify the user interface for students with special needs by limiting access to essential apps and features.
5.2. Retail
- Point-of-Sale (POS) Systems: Lock tablets to the POS app, ensuring that employees can only use them for processing transactions.
- Interactive Kiosks: Create interactive kiosks for product information, customer service, or self-checkout.
- Digital Signage: Use tablets as digital signage displays to showcase promotions, advertisements, or important information.
5.3. Hospitality
- Guest Check-in: Provide tablets for guests to check in and out of hotels or resorts.
- In-Room Entertainment: Offer tablets with pre-loaded entertainment apps and content.
- Restaurant Ordering: Allow customers to place orders directly from tablets at their tables.
5.4. Healthcare
- Patient Check-in: Provide tablets for patients to check in and fill out medical forms.
- Medical Information Access: Allow healthcare professionals to access patient records and medical information on secure tablets.
- Telemedicine: Use tablets for virtual consultations and remote patient monitoring.
5.5. Manufacturing
- Equipment Monitoring: Use tablets to monitor equipment performance and track production data.
- Quality Control: Allow employees to use tablets to record quality control data and report defects.
- Training and Safety: Provide tablets with training materials and safety guidelines for employees to access on the factory floor.
5.6. Transportation
- Electronic Logging Devices (ELDs): Use tablets as ELDs to track driver hours and comply with regulations.
- Navigation Systems: Provide drivers with tablets for navigation and route planning.
- Passenger Entertainment: Offer passengers tablets with entertainment options during long journeys.
5.7. Corporate
- Dedicated Task Devices: Lock down devices to specific work-related apps, like CRM or project management tools.
- Meeting Room Controls: Tablets controlling presentation equipment or video conferencing.
- Visitor Management: Streamline the visitor check-in process with dedicated tablets.
6. Ethical Considerations for Implementing Guided Access Alternatives
When implementing Guided Access alternatives, it’s essential to consider the ethical implications of restricting device usage. While these features can enhance security and productivity, they can also impact user privacy and autonomy.
6.1. Transparency and Consent
It’s crucial to be transparent with users about how their devices are being managed and why restrictions are being implemented. Obtain informed consent from users before enrolling their devices in an MDM platform or enabling Screen Pinning. Explain the purpose of the restrictions and how they will benefit the user or the organization.
6.2. Data Privacy
Be mindful of the data that is being collected and stored by the MDM platform. Only collect data that is necessary for managing and securing the devices. Implement appropriate security measures to protect user data from unauthorized access.
6.3. User Autonomy
Strive to balance security and control with user autonomy. Avoid implementing overly restrictive policies that prevent users from accessing legitimate apps or features. Provide users with options to customize their device settings and personalize their experience, within reasonable limits.
6.4. Accessibility
Ensure that the kiosk mode configuration is accessible to all users, including those with disabilities. Provide alternative input methods, such as voice control or touch gestures, for users who cannot use a traditional keyboard or mouse.
6.5. Regular Review
Regularly review the MDM policies and kiosk mode configurations to ensure that they are still relevant and effective. Adjust the policies as needed to address changing security threats and user needs.
By considering these ethical implications, organizations can implement Guided Access alternatives in a responsible and user-friendly manner.
7. Compliance Standards and Regulations
In many industries, compliance standards and regulations dictate how devices must be managed and secured. When implementing Guided Access alternatives, it’s essential to ensure compliance with these requirements.
7.1. HIPAA (Health Insurance Portability and Accountability Act)
HIPAA sets standards for protecting sensitive patient health information. If you are using Samsung devices in a healthcare setting, you must ensure that the devices are compliant with HIPAA regulations. This includes implementing security measures to protect patient data, such as encryption, access controls, and audit trails.
7.2. PCI DSS (Payment Card Industry Data Security Standard)
PCI DSS sets standards for protecting credit card data. If you are using Samsung devices to process credit card transactions, you must ensure that the devices are compliant with PCI DSS requirements. This includes implementing security measures to protect cardholder data, such as encryption, firewalls, and regular security assessments.
7.3. GDPR (General Data Protection Regulation)
GDPR sets standards for protecting the personal data of individuals in the European Union. If you are using Samsung devices to collect or process personal data of EU residents, you must ensure that the devices are compliant with GDPR requirements. This includes obtaining consent from users before collecting their data, providing users with access to their data, and implementing security measures to protect their data from unauthorized access.
7.4. Industry-Specific Regulations
In addition to these general regulations, many industries have their own specific compliance requirements. For example, the financial services industry has regulations related to data security and privacy, while the education industry has regulations related to student privacy.
MDM solutions can help organizations comply with these regulations by providing features such as:
- Data Encryption: Encrypting data on devices to protect it from unauthorized access.
- Access Controls: Restricting access to sensitive data and applications.
- Audit Trails: Tracking user activity on devices to identify potential security breaches.
- Remote Wiping: Remotely wiping data from lost or stolen devices.
- Policy Enforcement: Enforcing security policies on devices to ensure compliance.
8. Integrating Guided Access Alternatives with Existing Security Infrastructure
To maximize the effectiveness of Guided Access alternatives, it’s essential to integrate them with your existing security infrastructure. This includes integrating with your network security systems, identity management systems, and security information and event management (SIEM) systems.
8.1. Network Security Integration
Integrate your MDM solution with your network security systems to ensure that devices are protected from network-based threats. This can include implementing firewalls, intrusion detection systems, and VPNs to secure network traffic.
8.2. Identity Management Integration
Integrate your MDM solution with your identity management system to ensure that only authorized users can access devices and applications. This can include implementing multi-factor authentication, single sign-on (SSO), and role-based access control (RBAC).
8.3. SIEM Integration
Integrate your MDM solution with your SIEM system to monitor device activity and identify potential security incidents. This can include collecting logs from devices, analyzing the logs for suspicious activity, and generating alerts when incidents are detected.
8.4. Threat Intelligence Feeds
Integrate your MDM solution with threat intelligence feeds to stay informed about the latest security threats and vulnerabilities. This can include subscribing to threat intelligence feeds from security vendors and government agencies.
By integrating Guided Access alternatives with your existing security infrastructure, you can create a more comprehensive and effective security posture.
9. The Future of Device Restriction on Samsung Devices
The landscape of device restriction on Samsung devices is constantly evolving, with new technologies and features emerging all the time. Here are some trends to watch out for:
9.1. Enhanced Android Management APIs
Google is continuously improving the Android Management APIs, which allow MDM providers to manage Android devices more effectively. These APIs provide access to new features and capabilities, such as advanced kiosk mode settings, enhanced security policies, and improved device tracking.
9.2. Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML are being used to automate device management tasks and improve security. For example, AI can be used to detect anomalous device behavior and identify potential security threats. ML can be used to personalize device settings and provide users with a more tailored experience.
9.3. Zero Trust Security
Zero trust security is a security model that assumes that no user or device can be trusted by default. This means that all users and devices must be authenticated and authorized before they can access resources. Zero trust security is becoming increasingly important as organizations move to cloud-based environments and embrace BYOD (bring your own device) policies.
9.4. Biometric Authentication
Biometric authentication, such as fingerprint scanning and facial recognition, is becoming more common on Samsung devices. Biometric authentication provides a more secure and convenient way to authenticate users and protect sensitive data.
9.5. 5G Connectivity
5G connectivity is enabling new use cases for Samsung devices, such as remote monitoring, virtual reality, and augmented reality. 5G connectivity also presents new security challenges, as it increases the attack surface and makes devices more vulnerable to cyberattacks.
As these trends continue to evolve, organizations will need to adapt their device management strategies to take advantage of new technologies and address emerging security threats.
10. Conclusion: Finding the Right Solution for Your Needs
While Samsung devices don’t offer a direct “Guided Access” feature like Apple’s iOS, there are effective alternatives available. Screen Pinning provides a basic level of single-app mode functionality, while Mobile Device Management (MDM) solutions offer a more robust and comprehensive approach. The best option for your organization will depend on your specific needs, budget, and technical expertise.
If you need a simple way to lock a device to a single app for a short period of time, Screen Pinning may be sufficient. However, if you need to manage and secure a large number of Samsung devices, or if you require advanced features such as remote management, kiosk mode, and data encryption, an MDM solution is the better choice.
CONDUCT.EDU.VN is your resource for understanding the nuances of device management and compliance. Explore our resources to learn more about MDM solutions, security best practices, and compliance standards. Let us help you find the right solution to protect your Samsung devices and ensure a safe and productive user experience.
Need further assistance in navigating the complexities of device management and compliance? Contact us at conduct.edu.vn. Our experts are ready to help you find the best solutions for your organization’s needs. Visit our website or reach out to us at 100 Ethics Plaza, Guideline City, CA 90210, United States, or Whatsapp: +1 (707) 555-1234.
Frequently Asked Questions (FAQs)
1. Is there a Guided Access equivalent for Samsung devices?
While Samsung doesn’t have a feature named “Guided Access,” the Screen Pinning feature and MDM solutions provide similar functionality.
2. How do I enable Screen Pinning on my Samsung device?
Go to Settings > Security > Pin Windows (or App Pinning) and toggle the switch to enable it. Then, open the app you want to pin, go to the Recent Apps screen, and tap the app icon to select “Pin this app.”
3. What are the limitations of Screen Pinning?
Screen Pinning offers limited control over hardware buttons, doesn’t always require a PIN to exit, and is difficult to manage at scale.
4. What is MDM and how can it help with Samsung device management?
MDM (Mobile Device Management) is a software solution that allows IT administrators to remotely manage, secure, and monitor devices. It provides features such as remote configuration, security policies, kiosk mode, and device tracking.
5. What is kiosk mode?
Kiosk mode restricts a device to a single app or a pre-defined set of apps, making it ideal for dedicated-purpose devices.
6. How do I implement kiosk mode on Samsung devices?
You can implement kiosk mode using an MDM solution. Follow the MDM provider’s instructions to create a kiosk profile and deploy it to your devices.
7. What are the benefits of using MDM for Samsung device management?
MDM provides remote management, security policies, kiosk mode, device tracking, application management, and content management.
8. What are some examples of MDM solutions for Samsung devices?
Examples include Scalefusion, MobileIron, VMware Workspace ONE, and Microsoft Intune.
9. Are there any ethical considerations when implementing Guided Access alternatives?
Yes, it’s important to be transparent with users, protect their data privacy, respect their autonomy, and ensure accessibility.
10. What compliance standards should I be aware of when managing Samsung devices?
Relevant compliance standards include HIPAA, PCI DSS, and GDPR.